DeHashed is one of the most advanced and popular security and anti-fraud tools available online. This tool enables its users to search for and retrieve information from hacked databases.
The DeHashed platform works by letting its user find information that has been published or leaked by hackers by searching in various hacker databases.
It helps the users regain their leaked information quickly and avoid misuse by hackers or other harmful elements on the internet.
The platform is one of the fastest and the most significant search engines for data breaches. It is popular among its users because of the straightforward interface and the fact that it allows users to quickly and easily find their leaked information.
Even though DeHashed is one of the best information security and data breach tools, it is not the only one available. Other tools help you do the exact same searches and give you similar features and functionality as the platform.
One of the main reasons most people look for DeHashed alternatives is that they do not offer cleartext results but rather HTML-based results. This makes it difficult for users with very little HTML knowledge to view results unless they pay.
Another reason is that the platform does not offer specific results. Most of the search results are broad, making it difficult for users to see them easily.
Let’s find out some of the best alternatives you can consider.
Best DeHashed Alternatives
1. Snusbase
Information security and data safety and security are crucial in the current online technology world. This is the reason behind the development of Snusbase.
Like DeHashed, this is a reputable and trustworthy search engine for online data leaks. It enables its users to stay ahead of the latest data breaches.
Snusbase provides users with information and online security regarding their leaked information and indexes from various compromised sites. It allows you to search for information pertinent to you, such as hashes, emails, usernames, and passwords.
This platform stands out from others, including DeHashed, because it offers more targeted results to a user’s search. However, their databases are not as extensive as those of DeHashed.
In addition, the platform also offers its users a way of getting back control of their leaked data, information, and accounts.
Due to its unique features, it is no wonder why it is trusted even by some significant law enforcement and companies to protect and proactively take action against illegal information leaks and account takeovers.
Unlike some of its competitors on the market, Snusbase provides uncensored search results in cleartext form. There are free and paid plans for people looking to join Snusbase, with paying members getting access to all information regarding data breaches affecting them.
People and organizations can integrate their eternal security and monitoring suites using an API to help protect their data and information. It is also a very effective tool to protect against and investigate online fraud cases.
2. Spybot Identity Monitor
Spybot Identity Monitor is a tool that has been around for a while. It is an identity monitor with features to help its user find out whether or not their information has been shared or leaked online by hackers.
It is an easy tool that lets you monitor several accounts for data breaches and provides an overview of the known sources.
Although it gives users monitoring capabilities similar to DeHashed, there are some differences. First, Spybot Identity Monitor uses different databases to check for any information leaks. For example, it uses Have I Been Pwned databases for most searches.
It also has a standalone application, a Windows App, and an iPhone App, letting users access its functions on different devices. However, when it comes to maintaining a vast database of data breaches, DeHashed has more to offer.
The advanced technology used on the platform allows you to monitor your account details and information effectively and get notifications immediately your information and data are leaked anywhere on the internet.
The ability to get notified immediately after your data leaks is crucial since it allows you to quickly gain control of information or accounts from the hands of hackers.
People widely use it because of its simple, elegant, and intuitive interface. It is also easy to install and set up.
With its quick setup, the user only has to enter their account details. They get an overview of any breach or suspicious activity related to the information they have filled in.
3. LeakCheck
As far as trustworthiness and alternatives for DeHashed go, LeakCheck is a name to consider. The platform lets its users save the digital identities of individuals or organizations for monitoring purposes.
LeakCheck does not offer as many filters as DeHashed does when searching for leaks. However, it provides more accurate and detailed search results for a username and email than DeHashed.
It also does not display any results for free users to see. You have to pay for a plan, although they are very affordable.
The platform is valuable for companies and everyday individuals and developers since they can save their information and credentials and protect those of users utilizing their apps, websites, etc.
Additionally, members of LeakCheck can query for their information and get search results almost instantly. This is made possible by looking for leaked information in the platform’s databases and avoiding information from sources around the internet that contain your information illegally.
The platform maintains a massive database of leaked information and its sources to ensure that its user gets extensive protection and security. On top of this, users can also do bulk searches, which is very efficient, especially for organizations with many personnel.
4. Personal Data Leak Checker
Personal Data Leak Checker has built a name by providing users with a way to stay safe online and access the most recent database breaches. With a quick search, users can figure out what, if any, information is leaked.
Users can search for details such as email and phone numbers against their database to determine whether or not there is a leak.
The search parameters are not as broad as those of DeHashed. However, it displays results more targeted to the user’s email address than DeHashed.
DeHashed has a bigger and better database of hacked information than this platform. However, no one can complain about this since the website is entirely free to use.
It’s an effective tool to monitor and find hacked information. Any information leaked online is indexed by the platform and the details of where the leak originated.
5. Leakwatch
This is a Java API and command-line tool that is flexible and enables users to screen for any data and information leaks by Java programs they are using. It is an excellent tool for people looking to prevent their information from being compromised while utilizing the internet.
If any user information leaks, they will get a notification to indicate what is compromised. The platform goes a step beyond DeHashed by providing users with a team of experts to help them regain control.
Apart from the fact that there is no installation required, another significant benefit of the platform is its ease of use and availability of free membership. It also provides a way for you to set up a centralized platform to monitor any data breaches in your system.
Additionally, most users love the platform because there is a low chance of false positives in the alerts. Furthermore, with each detected leak, the user gets a report together with the best suggested actionable steps to take to help them mitigate risks and safeguard their information.
Even though it is a command-line tool, the user does not require extensive skills to use it. They can easily understand the metrics and insights provided by Leakwatch.
6. F-Secure Leak Checker
This online platform ensures its users’ digital privacy and security. F-Secure Leak Checker has one of the broadest databases of leaks collected from the internet.
F-Secure’s Leak Checker is a free-to-use tool, unlike DeHashed, where users have to pay to access some features and services.
While DeHashed offers a variety of parameters for users to search, this tool only allows users to search using an email address. However, users should expect this since they do not have to pay anything to see their query results like they would have to when using DeHashed.
Unlike DeHashed, it does not show the leak’s origin. However, its results to the users are more targeted to their search than DeHashed.
7. Mypwd
Mypwd is a platform designed to safeguard and check whether hackers have compromised your passwords or email. This intelligent platform uses a more functional process to proactively protect its users whenever their information and data are leaked.
It only lets users search for data leaks using only their email address, unlike DeHashed, which allows for different filters. However, this platform offers better search results and in cleartext, making it easier for users to understand the results better than DeHashed.
With a comprehensive database of more than nine billion leaked files, users are more likely to find out whether or not their information has been hacked.
Even though they have an extensive database, it is not as comprehensive as the one DeHashed operates. Despite this, they offer more accurate information on available leaks than DeHashed.
Not only this, but the platform includes a report of the origin of the leak, making it possible for the user to regain control of their information while also providing an easy way to start an investigation into the leaks if need be.
Mypwd offers functionality and features that help to combat cybercrimes, such as data and identity theft, bank scams, and offenses people perpetrate via chat applications. The platform uses an AI capable of scanning for internet and dark web leaks.
8. Inoitsu
This email breach analysis platform allows users to determine whether their email addresses have been pwned. The application interface is simple to use and only requires that the user fills in their email address in a search box and hits the submit button.
Within seconds, the user can determine if their email address has been breached or not.
Unlike DeHashed, users cannot use anything other than an email address to search their databases. However, it is a good alternative for people who cannot afford to pay for DeHashed plans as a free tool.
Furthermore, users also get a report outlining how vulnerable their email addresses can be compromised. Their reporting is just as detailed as DeHashed’s.
This summary report is crucial for users since it enables them to take better measures to safeguard their emails from hackers. For example, they may do so by updating their passwords to be harder to hack.
The platform helps protect its users by using searches on its databases and reports from multiple other platforms. Finally, besides this being a safety and protection tool, it is also an educative one where users get guidelines and tips to help better protect themselves and safeguard against fraud.
9. Firefox Monitor
It is essential for security and data breach monitoring tools to be lean and lightweight to work fast and provide instant results. This is what Firefox Monitor provides its users.
Firefox is a name that is synonymous with some of the best web services and tools, and it is the same dedication that has gone into developing this tool. The platform uses a conventional approach to mitigate any risk to your data from hackers.
It is not only a safeguarding application but also a monitoring tool that notifies its users if any breaches have occurred so they may take necessary steps to protect themselves. Firefox Monitor provides current and past breach reports based on your personal information to your data.
Firefox Monitor, unlike DeHashed, does not have its database of data leaks and has to rely on those provided by third parties. However, The platform gives better insights into the leaks and is very helpful in assisting users to regain control.
Like most software applications developed by the company, this tool has a simple and user-friendly interface making it easy to use even for complete beginners.
10. Sophos UTM
This is among the best gateway threat management systems available for online devices. It is a tool that works in the background of your system, monitoring all traffic going through it and assessing it for potential risks.
The tool provides its user with many features and functionality such as remote routing access, VPN servers, a translation server for your network address, and many more options to ensure all its users are safe while using the internet. It offers more features than DeHashed.
With an excellent firewall system designed to inspect all network traffic passing through your system, this tool is invaluable for users to safeguard against privacy and security breaches.
Other prominent features of the application include content filtering, web caching, better network performance, and layer protection, to name but a few.
As far as complete security and breach monitoring platforms go, Sophos UTM is a leader. It offers users various ways to customize their security measures and restrict the ease of access by suspicious traffic from the internet, something DeHashed does not.
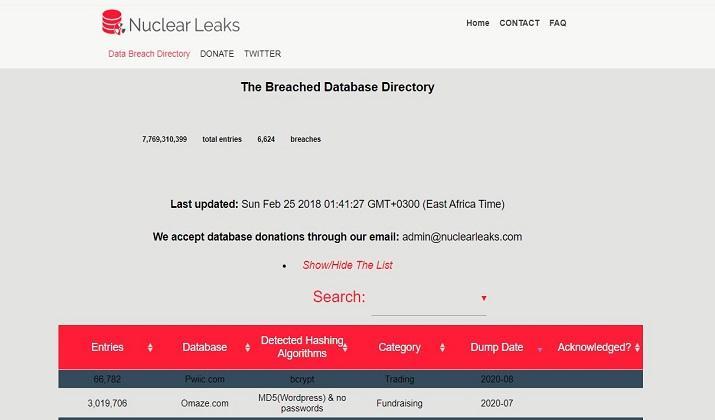
11. Nuclear Leaks
This excellent and sophisticated platform offers users a vast collection of databases to search for any leaked or hacked information about their identity. Many individuals, including journalists and security experts, use this platform to look for leaked information.
Nuclear Leaks is not just a search engine for data leaks; it is also a tool to monitor any potential risks to your information. Whenever your information has been leaked and is available online, you will instantly get an alert notifying you of the presence of a leak and how you should deal with it.
Nuclear Leaks databases are not updated as regularly as those of DeHashed. Despite this, the platform provides a better alert system than DeHashed if your information is leaked.
Like DeHashed, users can search for information such as addresses, emails, usernames, phone numbers, and keywords against a database with leaked data.
In addition to this, the platform does provide additional information about data leaks like hashing algorithms used, dump dates, categories of the dumps, and total entries.
12. WeLeakInfo
This intuitive platform gives its users data breach services. The platform’s database has over eight billion records and is constantly updated to ensure users have the latest data leaks.
Unlike DeHashed, WeLeakInfo does not censor the data on its databases, ensuring that users can quickly see what data leaks and their sources. The platform allows for integration with other applications and websites, enabling people to search for and find leaked information.
People using the public API can search for information, including email addresses, phone numbers, passwords, IP addresses, or any keyword.
It also lets users carry out regex and wildcard searching, enabling them to get additional information about leaks.
Even though the platform is not as popular as DeHashed, it provides more information about your leaked information than DeHashed.
13. Bitwarden
This is different from most DeHashed alternatives because it is more of a password manager. However, it does provide its users with a way to protect their saved passwords by encrypting them using a proprietary algorithm.
The platform works for a user to log in to their favorite websites with their accounts, and at the end, they will be asked to set a master password. It is this master password that Bitwarden then uses to log you into its platform and all other connected accounts.
The tool will monitor any suspicious activity and login attempts to all the accounts you connected with the user. In case there is any risk, they will notify the user immediately.
Like DeHashed, this platform has built a reputation and credibility in the security industry. Big companies using this platform include the University of Toronto Press, Intesys, and Glovo.
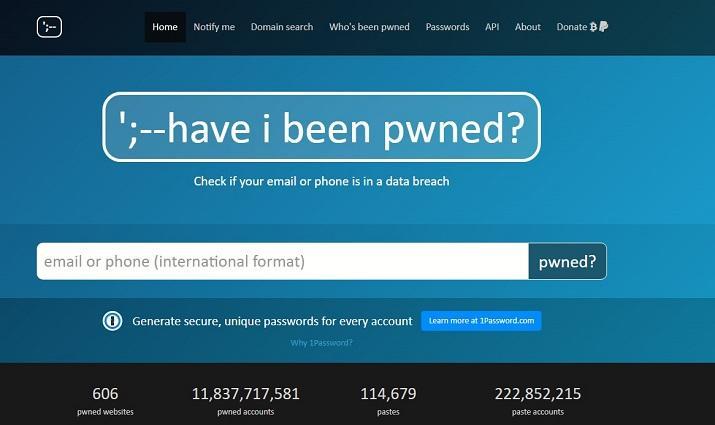
14. Have I Been Pwned?
This tool lets users discover whether any personal information is breached and leaked online. It is an excellent tool for people looking to determine if the information attached to their email address has been compromised.
The platform does not allow for a wide range of search parameters like DeHashed since users can only use an email or phone number to query their databases. However, it gives users more targeted search reports than DeHashed.
Furthermore, the platform has high-level encryption algorithms to safeguard the information users provide when carrying out queries.
Statistics about the number of compromised websites and emails are displayed. These stats are only for the records in their databases.
This platform does not have the sources of its leaks and operates by importing updated leaks on DeHashed databases. Due to this, it provides the same results as one would get if they search a compromised email on DeHashed.
15. BreachDirectory
This is an excellent and credible platform where users can input their personal information and determine if any usernames, emails, or phone numbers related to the search are compromised.
This platform does not offer a comprehensive way to search for leaks since they offer fewer search criteria than DeHashed. However, this is expected since it is a free tool, and users do not have to pay anything to view search results.
If there is a hit in their database, BreachDirectory will show the user which information and to what extent. Any leaked search is highlighted in red, making it easy to see.
The platform continually searches information the user has provided against its databases and notifies them if there are any matches.
The company often updates BreachDirectory databases with leaked information found all over the internet. This ensures that its users get the best monitoring and safeguarding capability.
Conclusion
By far, the best alternative to DeHashed is Snusbase. Even though Snusbase does not provide a comprehensive database like DeHashed, it offers better search results.
Search results displayed by Snusbase are more targeted to the user’s search parameters and are more accurate and easy for the user to understand. Also, the results are in cleartext form.
Lastly, API integration with other services and platforms is more seamless than DeHashed.
Cassie Riley has a passion for all things marketing and social media. She is a wife, mother, and entrepreneur. In her spare time, she enjoys traveling, language, music, writing, and unicorns. Cassie is a lifetime learner, and loves to spend time attending classes, webinars, and summits.